Regular readers will know my views on the validity period of TLS certificates, and how they definitely need to be made shorter than they currently are! We made some good progress on reducing their lifetime over the last few years, but recently, that progress seems to have stalled out... Well, now, we might have our first glimmer of hope!
The story so far
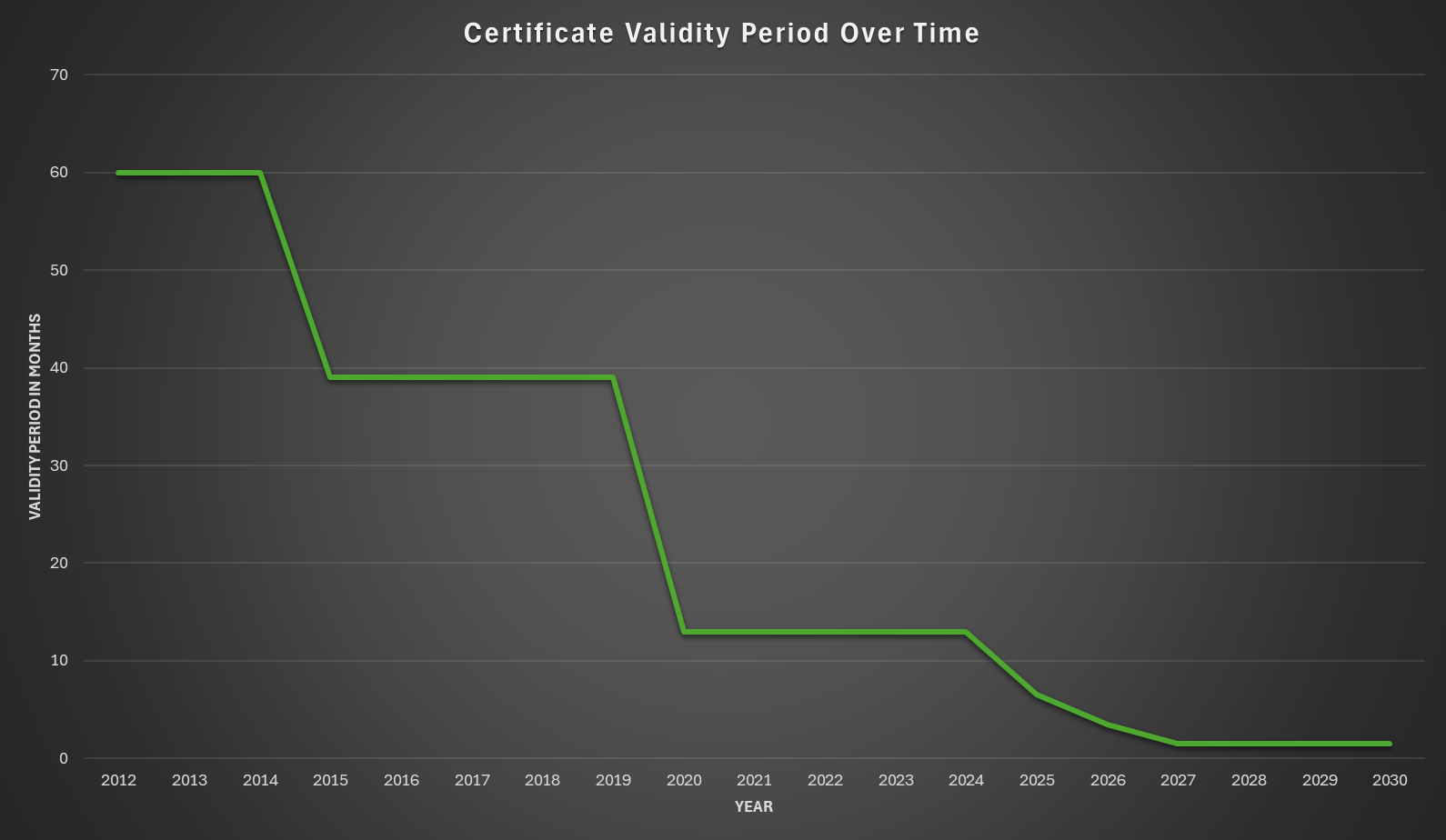
There's a lot of really good information out there on this topic, and I myself have covered this in various ways over the years. I'd definitely recommend my post on Cryptographic Agility as a good starting point, but I will pull the most pertinent information out into this post here. Looking at the historic reductions to certificate lifetimes, we can summarise them as the following maximum limits and when they were introduced:
- 2012 - 60 months
- 2015 - 39 months
- 2018 - 825 days
- 2020 - 398 days
That means that right now, the longest a certificate can be valid for is 398 days total. If you look at the cadence for change there, you can also see how we fell of the pace a little as an industry, and I've long been waiting for the announcement of the next change. Well, we don't have to wait any longer!
SC-081: Introduce Schedule of Reducing Validity and Data Reuse Periods
You can go and read the full details of the proposed ballot yourself, but let's just dive straight into the good stuff because I'm too excited to delay any further. (Also, please drop by that page and give a 'thumbs up' response to show some support!)
Here's the data from the ballot that will show how, over the next 3 years, it is proposed that we continue our efforts to reduce certificate lifetimes and improve the security of the ecosystem. I've put it in a table to make it easier to digest, and here it is!
Update 14th Nov 2024: the below table and text has been updated to reflect changes to the proposal. The first reduction to 200 days is now proposed to land in March 2026, 6 months later than originally planned, along with the second reduction to 100 days also being postponed by 6 months. The final reduction has changed from being 45 days maximum validity to 47 days maximum validity, and was delayed even further by 11 months until March 2028.
| Certificate issued on or after | Certificate issued before | Maximum number of days for validity |
|---|---|---|
| March 15, 2026 | 398 | |
| March 15, 2026 | March 15, 2027 | 200 |
| March 15, 2027 | March 15, 2028 | 100 |
| March 15, 2028 | 47 |
First of all, this does mean that nothing will happen for almost 18 months... A shame, yes, but, I can also understand why. It's nice to give the industry time to plan and prepare for a change, and, the first change is also a smaller change too.
It's from March 2026 that change starts happening, with the new limit of 200 days on certificates. That still leaves certificates valid for a really long time, so is a gentle introduction into the reduction schedule.
This is followed by a 100 day limit on certificates a whole year later in March 2027, so again, another huge period of time to plan and prepare for the next change.
Finally, we arrive in the distant future of March 2028, when the 47 day lifetime limit will be introduced! At this point, fully automated certificate renewal is obviously the goal, and the path to get there has now been laid out.
What does this mean?
It means that we're finally making the progress we need to make as an industry. It means that someone has finally been willing to be the person that steps forward and proposes the changes we need, saying the things that need to be said, but that many won't like.
For so many years now, in both of the training courses that I deliver, I've been telling people and organisations that certificates are only going to get shorter, because they simply need to!
If you haven't been preparing for automation in your certificate renewal processes already, you've missed the writing that's been on the wall for many years now. Certificates have only ever gotten shorter as time has gone by, and key industry players have been pushing for shorter certificates for a long time. If you haven't started working on automating your certificate renewal processes, then you should. The best time to start that work was yesterday, the next-best time is today, and the worst time is tomorrow.
Will this ballot pass?
Thus far, the reaction to this proposal has been exactly what I expected it would be. Those that are looking forwards and to the improvement of security are supportive, and those who are not prepared or willing to change are resisting. I'm hoping that the gradual introduction of these changes, with a nice, steady and predictable timeline will help to sway some to do the right thing, but we're just going to have to wait and see how the vote goes. If we graph the proposed changes, and look at them alongside historic changes, we can see that this is a very reasonable plan being proposed.
We should also consider what has happened in the past when this industry desperately wants change for the better, but commercial entities have tried to hold us back, being swayed by their profits rather than what's best for the average Internet user. I have my fingers crossed that we can get this done, but only time will tell... 🔒🌍✅
