With TLS having taken some great steps forwards in recent years, with TLSv1.2 in 2008 and TLSv1.3 in 2018, it's time to start dropping support for the legacy versions of TLS.
Legacy TLS
TLSv1.0 was released in 1999, that's more than 20 years ago(!), and TLSv1.1 was released in 2006, more than 14 years ago. It's fair to say that both of these protocol versions are old, really old. With the standardisation of TLSv1.2 in 2008 we took a really big leap forwards not only in the security the protocol offered but also the performance of the protocol. In 2018 we took an even larger leap with TLSv1.3 making yet more significant leaps in security and performance. For these reasons, it's time that the older versions of TLS were laid to rest before they become too old and weak and end up broken whilst we're still using them.
How widely used is Legacy TLS?
If we look at the data, how much impact would removing these legacy versions of TLS have. There's some good data gathered from SSL Pulse and we can see here the best version of TLS supported by sites scanned.
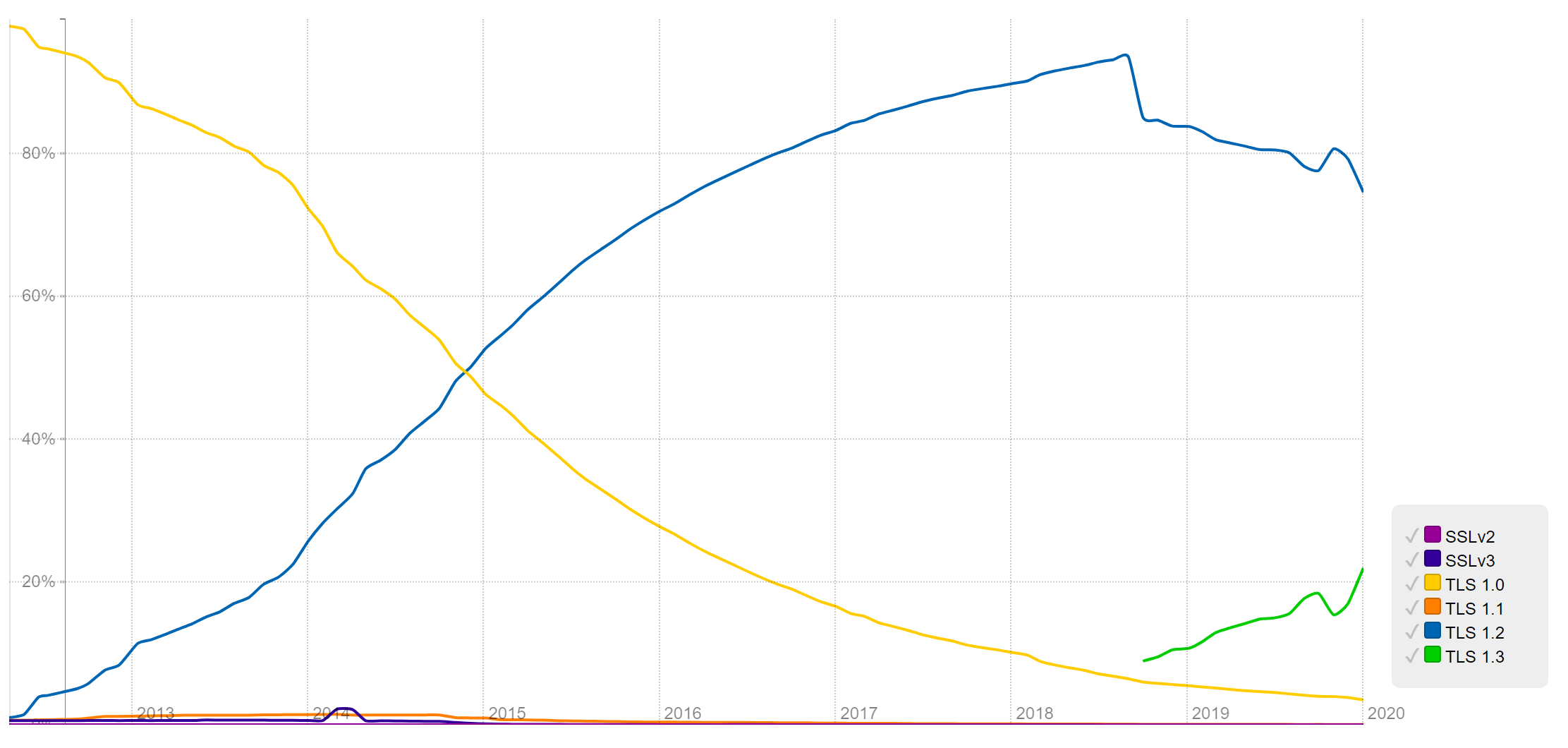
We see that during the massive rise of TLSv1.2 it was TLSv1.0 taking a fall, not TLSv1.1 as you might expect. TLSv1.1 is that little orange line running along the bottom that barely moved this whole time. It seems that removing TLSv1.1 is likely to be a minor issue because it was never really widely used and TLSv1.0 is still tailing off with a small amount of sites depending on it. If we take a look at my own data from Crawler.Ninja we can also see that most of the sites in the top 1 million sites on the Web won't be affected by this change.
Protocols:
TLSv1.2 319,357
TLSv1 2,580
TLSv1.1 41It shows the vast majority of sites are already on the newer TLSv1.2 and only a small fraction are depending on Legacy TLS as their highest supported protocol version. It's worth noting that my crawler doesn't support TLSv1.3 yet so there's a good chance some of the TLSv1.2 sites could upgrade even further, however for the purposes of this blog post, that's not really a problem.
Why do we need to change?
Well, as I said, it'd be good to remove these legacy versions now but it's more important we upgrade to support higher versions and we do have some encouragement beyond me telling you it's a good idea. Chrome is now warning users about sites that they visit that are using either TLSv1.0 or TLSv1.1 for the connection.
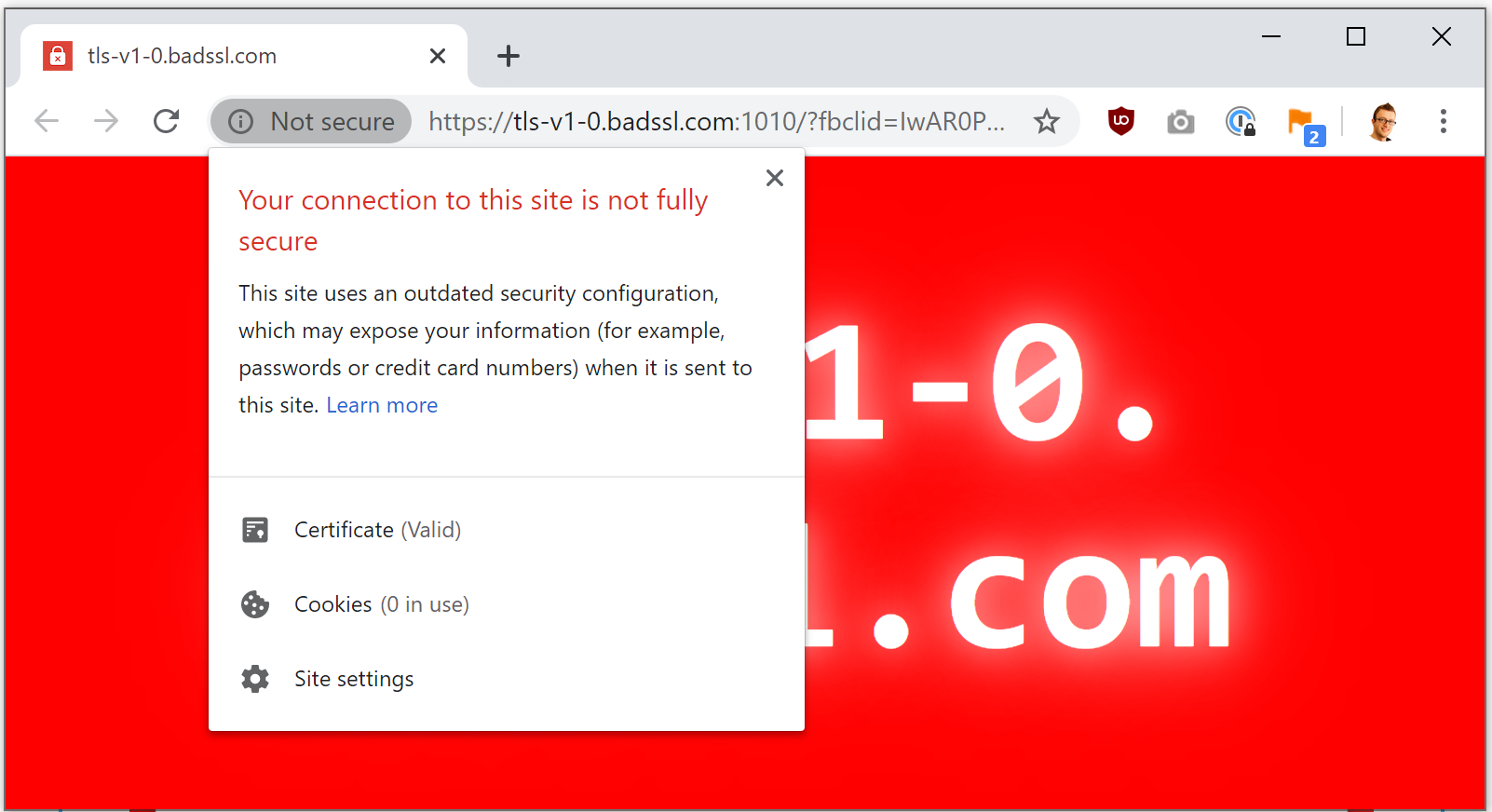
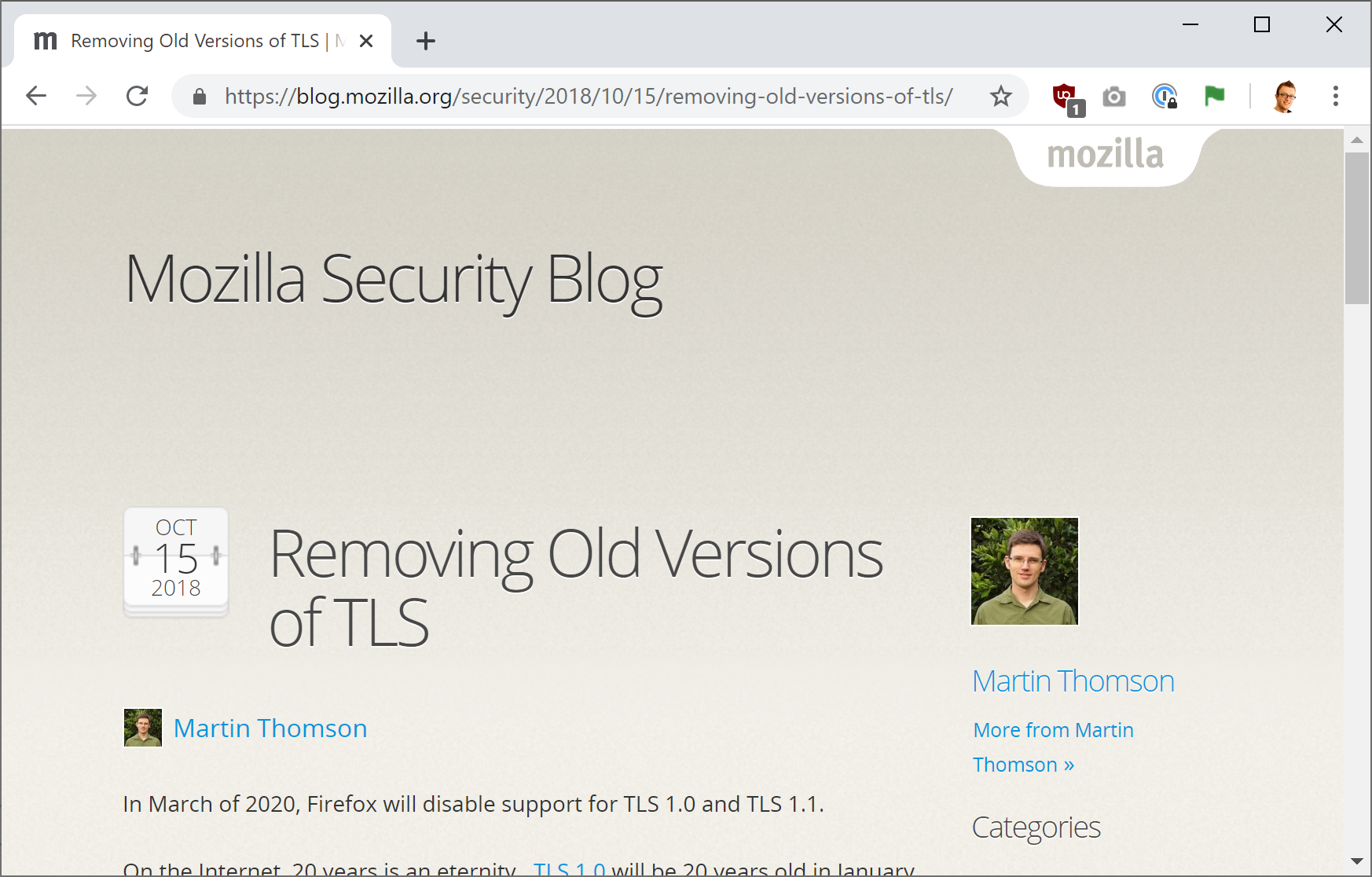
You can visit the Bad SSL test site for yourself to see the warning if your version of Chrome is up to date. It's not just Chrome either, Firefox announced they are going to drop all support for both TLSv1.0 and TLSv1.1 in March 2020 and they announced this all the way back in October 2018!
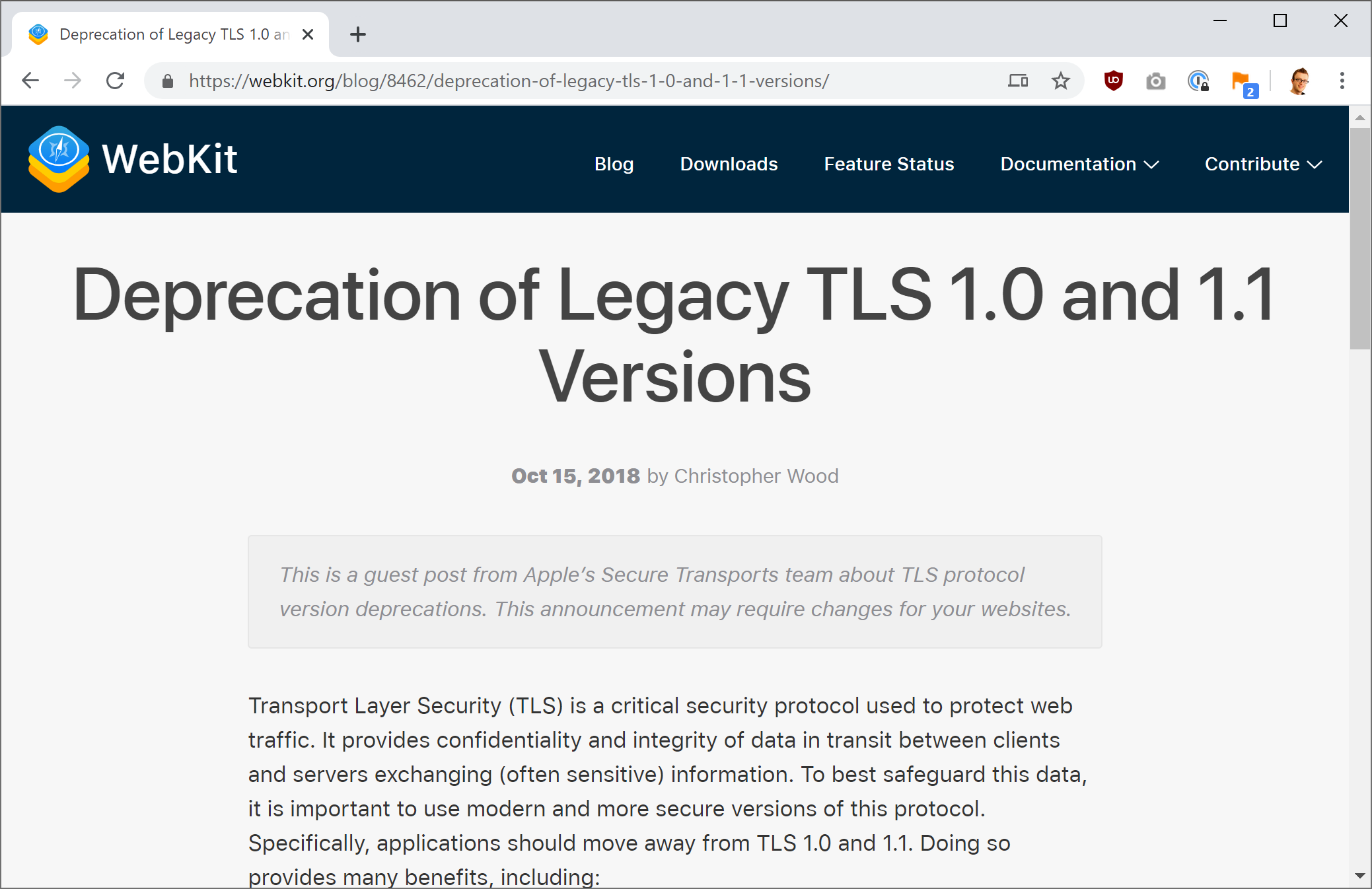
Just to make it a trifecta, Safari will also be dropping support for Legacy TLS on the same timeline too. I wonder if all of the browser vendors thought this was a great idea and worked together to make it happen... 🤔
What you need to do
You need to update all of your services to use a minimum of TLSv1.2 for secure connections. I wrote about this impending deprecation a while back and I'm using a Cloudflare Worker to notify visitors to my site if they are using a client that requires either of these Legacy TLS versions. Remember, it's not just about your site being able to support TLSv1.2, the client has to be able to support it too! You can see my blog Deprecating TLSv1.0 and TLSv1.1 gracefully with Cloudflare Workers and this is the warning shown to those clients.
Now remember, you don't necessarily have to remove support for these Legacy TLS versions, you simply have to make sure that you support at least TLSv1.2 for clients like Chrome/Firefox/Safari to be able to connect. They will connect with the newer protocol versions and you won't see any connection issues or warnings. Older clients, like browsers that haven't been updated, that connect with Legacy TLS will still be able to connect and won't show warnings either because they won't have received the update to do that yet. My current plan of action is the following:
1) Support both TLSv1.2 and TLSv1.3 so modern clients can connect with the best possible protocol.
2) Continue to support Legacy TLS for any legacy clients that may be connecting.
3) Show deprecation warnings to clients using Legacy TLS so they know they need to update.
4) Eventually remove all support for Legacy TLS.
The exact date that you decide to implement point 4 is really up to you but you need to have implemented, or be implementing, points 1-3 now. Bear in mind that at some point in the future a critical issue could be found in either of the Legacy TLS versions that forces you to immediately drop them. It'd be best to put a date on that and I think that 1 year after their deprecation in the mainstream browsers is a pretty good target. We have to get these old clients updating before it's too late and security issues start creeping in to force the change. Time to get updating!
