CAA is a new mechanism that will allow site owners to specify which Certificate Authorities are authorised to issue certificates for their domain name. It's a simple DNS record so setup is a breeze and SSL Labs is now checking for it, so it's time to do it!
Why we need CAA
A Certificate Authority (CA) is an all powerful entity that can issue certificates for literally any domain on the planet. As the use of HTTPS, and thus certificates, is skyrocketing across the web (link)(link), we're looking to tighten up the controls on the CAs that issue them. Certificate miss-issuance, where someone else gets a certificate for your domain, is a really bad thing. Most of the time you won't even know this has happened so you can't take steps to remedy the problem. The Chromium team are pushing Certificate Transparency hard and have announced that CT will be required from Sept 2017, but CAA takes a different approach. CAA is designed to stop miss-issuance before it happens.
How it works
The most simple description of CAA is that it's a DNS record that lists the CAs permitted to issue certificates for your domain. A CA will be required to check this record before they issue a certificate and to only issue the certificate if they are authorised to do so. Of course, the most obvious thing to note here is that if a CA goes rogue and chooses to ignore the CAA record they can issue whatever certificates they like and we can't stop them. Also, in the event of a total compromise of their systems an attacker would still be able to issue a certificate for a domain they do not control. That said, there are still a lot of scenarios where CAA is useful. We've seen a few problems with CAs in the past where their verification checks or web GUI have been bypassed by simple bugs and their issuing systems then spit out a valid certificate to the attacker. There's also a whole compliance aspect to this where organisations could prevent staff from obtaining certificates from a CA like Let's Encrypt (who incidentally already support CAA) by restricting issuance to their 'preferred' CA. CAA is not a silver bullet but it is another layer in our defence. We don't have to worry about vendor lock because the record is only checked at the point of issuance and it couldn't be simpler to setup. There's really nothing to lose.
Setting up CAA
The minimal setup required for CAA is to just declare the CA or multiple CAs that you authorise to issue certificates for your domain. You do this with the new DNS RR that has been created. There is an awesome tool over on sslmate called the CAA Record Generator which does exactly what it says on the tin! Simply head over to the site, add your domain name, select the CAs you wish to authorise, a reporting address and that's it.
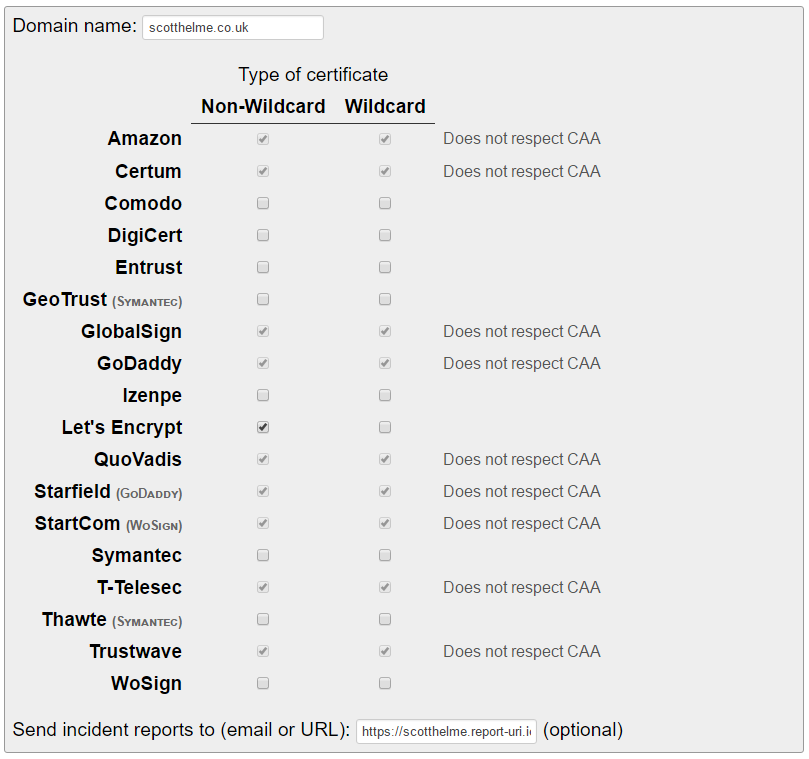
The tool will automatically generate the appropriate record/s for you and all you have to do now is create them in the DNS.
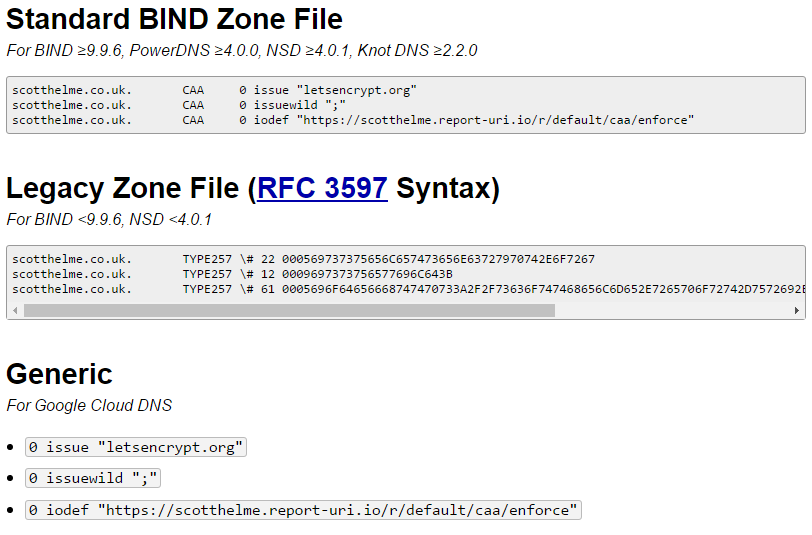
CAA Checking Required
Right now it's optional for a CA to check for a CAA record but the CA/Browser Forum have literally just voted to make this check mandatory in the Baseline Requirements. This will land on September 8th 2017 so if you setup your record now the CAs that already check will respect it and later this year all CAs will be required to respect it.
