Match.com is recognised as the largest online dating site in the world. Available in 25 countries and 8 different languages, it has millions of users in the UK alone. Having such a huge and purely online presence, the average person would be forgiven for thinking that security and privacy would be top of the agenda. With hacks and data leaks being so prevalent in recent news, I decided to take a look at the security over at Match.com.

Introduction
In recent weeks there have been some very high profile and damaging hacks. Adobe were hacked and exposed 153 million user credentials, MacRumours lost the account details of 860,000 users and Cupid Media lost the plain text credentials of 42 million dating website users. My first concerns about security over at Match.com were brought about when someone forwarded me an email they'd received containing a fairly large amount of personal information, about someone else. Now, I realise Match.com can't be held responsible for someone entering the wrong email address at sign up, but there's just no need to send things like their name, address and other details via email after signing up. This prompted me to take a look if this was just a one off, or the start of a trend.
Account Creation
As far as bad trends go, loading a login form over http:// and then using a POST request to https:// is pretty much up there with the worst. Loading sensitive data like a secure link over http:// opens up attack vectors for a malicious third party to rewrite the data in transit. My previous blog about TLS and data integrity covers this concept in a lot more detail. Here you can see the Match.com home page loaded over http:// with the login and sign up forms.
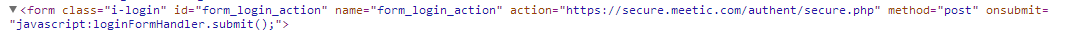
If we view the source on the page we can see that they are indeed issuing a POST request using https:// to the appropriate page.

Using Fiddler, or any other intercepting proxy, it's possible to modify these pages in transit because they aren't loaded over a secure connection. A simple Fiddler Script can quickly remove the security on these two forms.

Once Fiddler has access to my network traffic it can work its magic and remove the security from the sign up and login forms.
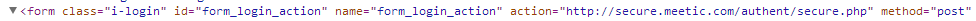

Now that we have modified the page our victims will sign up or login to Match.com and their browser is going to submit their credentials in the clear, without any encryption. Even if the pages at the other end enforce security and issue a redirect back to the secure version, it will already be too late. I was going to go right ahead and sign up to demonstrate, but there seems to be a problem.
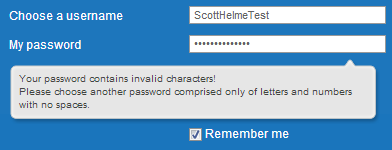
Oh dear. For some reason it seems Match.com doesn't like strong passwords, like those generated by my password manager (yes I used it even for this). You're only allowed to use letters or numbers and no spaces. There's also another problem here that they haven't informed me about. My password manager generates random passwords that are 24 characters in length and that field only contains 15 characters. After trying to paste my password again and trying to manually insert more characters it's apparent that they have limited the field to only allow 15 characters total. To confirm this I took a little look in the source of the page and there it is, a max length restriction.
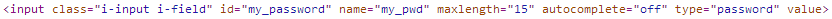
So, not only are we not allowed to use symbols in our password, like most websites seem to be telling us to these days, it's also limited to 15 characters without you being told. That's some pretty hefty blows to password strength. I checked if they enforce a minimum password length and was really pleased to find that my password only needs to be 4 characters long! Oh, and they tell me about the max length restriction too.
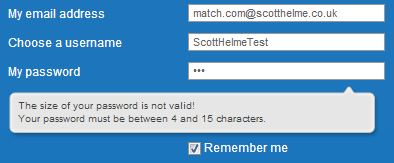
Right, I've reduced my password to only 15 characters and substituted the characters they don't like for letters or numbers. The sign up button has been pressed and I need to verify my email address using the link they just sent me. I suspect that some of you know what's coming...
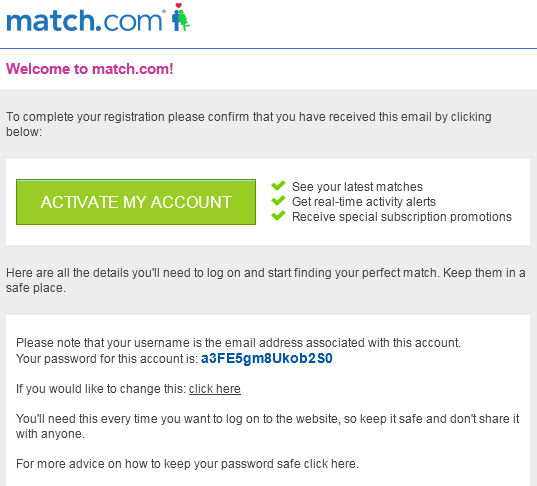
Yep, that's my password. Right there. In plain text. Via email. So, what's wrong with that you might think. Well, emails aren't a secure form of communication. This is largely the reason why companies like your bank will tell you to never send any sensitive information in an email when they contact you. At this point I can't be entirely certain about how they are storing the password, they do have access to the plain text prior to storage, so they could have emailed it to me then. Kind of contradictory though that I'm advised not to share my password with anyone and given a link to some advice on how to keep my password safe. Perhaps Match.com should read their own email, eh! "Don't share it with anyone", except anyone that has access to your traffic on the transport later, of course...
Emails with login links
Within minutes of signing up I started to receive emails about people viewing my profile. In each email there was a link to the Match.com site prompting me to go and look who had viewed my profile. Being naturally sceptical of any link I receive in an email I inspected it prior to clicking on it.
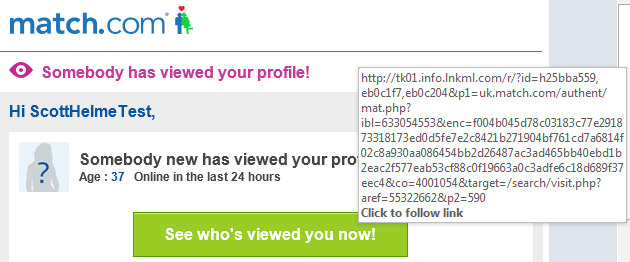
It seemed like an awfully long link just to take me to an account page on Match.com so I guessed it must contain some form of auth token to log me in to my account. To check I opened an Incognito Window in Chrome to navigate to the page without having any of my existing cookies interfere with the process. The link logged me straight in to my account without needing any user credentials.
Sending a link like that is fairly dangerous though I'll admit it's not quite as bad as sending me my password in an email again. If an attacker has access to my traffic or somehow gets hold of the email, they could have as much fun as they like with my profile and private information in my account. As the emails kept rolling in, I started noticing something they all had in common. The login link in each and every email was the same. These were not single use login links and appeared to provide permanent access to my account once you click them. This makes them even more dangerous in the hands of an attacker.
Password storage and reset procedures
I was a little concerned earlier about my password being sent in an email because they are not secure, but there's also another reason. If a password is properly handled it should be hashed prior to storage which means that the original password is safe and almost impossible to recover. When you come to login the site simply hashes the password you provide and if the hashes match, then the original passwords matched. They can verify your password without ever knowing what it was. The first indication that passwords aren't properly stored comes on the account page.

For some reason Match.com shows you what the first character of your password is on the account page. Now, that means they either stored a copy of the first character of my password on account creation, and then securely hashed my full password, or, the password is stored in plain text or using reversible encryption. The feature of showing me the first character of my password once I've already logged in seems fairly pointless and because this page is loaded over http:// it means that it's also visible on the transport layer, along with my session id. Couple that with the restrictions on your password when creating an account and this single character actually weakens your password considerably by reducing the possible 15 character password down to 14 characters. The password reset form is also loaded over http:// with a POST to a https:// address that can be stripped out. On the bright side they don't seem to have emailed me my new password when I reset it.

Forgotten passwords
The real way to check if a site is storing your password properly is to go through the forgotten password process. If your password is properly stored then it should be impossible for the site to recover it. If the they are using poor security, or no security at all, it will be possible for them to recover your original password. Given that I received my initial password via email when I created my account I wasn't surprised when this email popped up in my inbox.
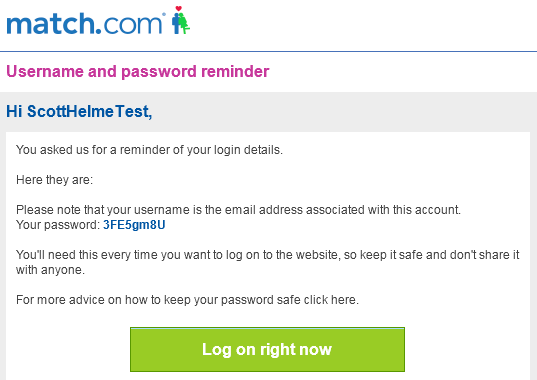
So, the likelihood is that there is no protection whatsoever on passwords in the database and they are stored in plain text. This presents a pretty significant lapse in security and should an attacker ever gain access to the database they would be able to scoop up potentially tens of millions of email addresses and passwords in one go.
There's that login link again
A common thing I have noticed through all the emails I have received from Match.com is that they all contain the same login link. I don't just mean the same button, I mean the actual link itself is identical in every mail. Even in an incognito window with no cookies the link logs me in to my account. A link like that should really be randomly generated and single use, at most, to allow the user to login only once. Having reset my password and been provided with the same link in all my prior emails, this is clearly not the case. This link is obviously a permanent feature and at the time of writing it has survived for almost 8 weeks and multiple password resets. If an attacker got hold of this link and started doing malicious things to your profile, the first thing you would probably do is reset your password to lock them out. Unfortunately, this would have absolutely no effect and at that point all you could do is contact Match.com to see if they could resolve the issue manually, or delete your account.
Remember me
Whilst looking through the cookies I was issued when using the 'Remember me' feature I noticed something that seemed familiar.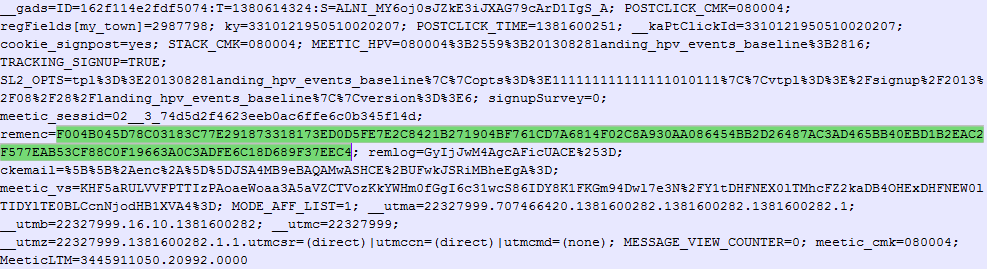
It's the exact same value that is embedded in the URLs for all the login links that came via email. Rather than using a unique and randomly generated token to identify the user it seems you are assigned a permanent token that is used across the board. Once this value is obtained by an attacker it permanently compromises your account. Having a fixed value as your proof of identity and then sending that value across the Internet with no transport layer security can only end badly.
Conclusion
There are a few basic security precautions not being taken on the Match.com site and the most notable is that passwords aren't stored properly. For a site that boasts such a high number of users, a breach could have far reaching consequences. I did inform Match.com of my findings on 2 occasions, but in the weeks that have passed I haven't even had a response to my emails. Let's hope that Match.com isn't in the headlines in the coming weeks.
